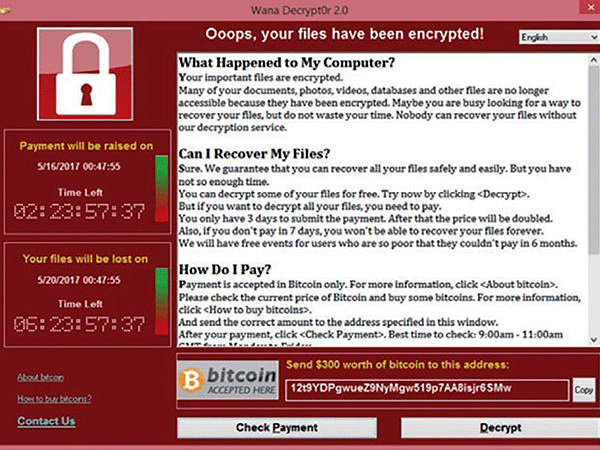
 |
| WannaCry lock screen. |
Huawei introduce to you anti ransomware solution (volume 1) What is ransomware?
Introduction
Ransomware refers to a malware virus that encrypts and restricts victims’ access to critical data (documents, emails, databases, source code). This data is only decrypted after a ransom is paid, hence the name.
Through this practice, cyber criminals often successfully extort money from individuals or organisations, marking the shift of ransomware becoming more than just malware, and into a highly-profitable business model.
Ransomware targets could be any business or organisation. Growing ransomware attacks are one of the most serious threats to global network security, with the World Economic Forum’s Global Cybersecurity Outlook 2022 reporting “ransomware attacks are at the forefront of cyber leaders’ minds.” This calls for a practice data security system deployed in conjunction with an emergency response plan to handle ransomware incidents before they threaten enterprise business.
The Evolution of Ransomware
Over the past 30 years, ransomware has gone through several stages, in which its attack scope and field have expanded from a single device, industry, or country, to every industry and business around the world. Today, ransomware attacks are increasing in scale and frequency at an alarming pace that quite simply, any enterprise or organisation can be targeted. Let’s look at its development in the past 15 years.
Maturity
Starting from 2009, and the rise of virtual currencies like Bitcoin, which created the conditions for new ‘active’ cyber extortion practices. Virtual currencies can be manipulated to ensure anonymity and make transactions untraceable, while the global circulation of virtual currencies has facilitated the ease of cross-border transactions, and accelerated the spread of ransomware. This period is best represented by the CryptoLocker Trojan, an email-based virus that shocked the world in 2013. Once in the system, this virus encrypted specific key files and demanded a total value of 41,000 Bitcoins. Since then, the number of ransomware families has grown rapidly between 2009 and 2015, with Bitcoin gradually becoming the preferred payment method for extortion attempts, and ransomware being pushed to the forefront of public security concerns.
 |
| |
Outbreak
Since 2015, our markets and industries have been crippled by damaging attacks. In 2017, WannaCry swept the globe at unprecedented scale, targeting Microsoft system vulnerabilities, that forced government, finance, electricity, and communications sectors in countries like UK, France, Spain, and Russia to stop production, and all within just five hours. WannaCry rendered devices useless for approx. 300,000 users in 150 countries and regions and caused total losses of US$8 billion.
How Ransomware works?
It is important to understand the methods that attackers use to spread ransomware to defend against ransomware.
1. Brute-force cracking:
Brute-force cracking is the simplest and most direct way to invade a system. It relies on tools to scan vulnerable ports exposed to the Internet for servers, individual users, or specific targets, and use Remote Desktop Protocol (RDP)-based weak passwords, penetration, and vulnerabilities to obtain corresponding permissions and launch attacks. Weak passwords in user systems are vulnerable to brute-force cracking. Ransomware is most commonly spread through brute-force cracking of RDP services, for example, NotPetya, a virus that cracks passwords and spreads over LANs.
Typical variants: NotPetya, Crysis, and GlobeImposter
2. Phishing emails
Ransomware is often spread though phishing emails. Through social engineering, attackers send fake emails to victims, and add malicious attachments or URL links disguised as legitimate files. When the recipient opens the attachment, the ransomware is quietly downloaded and starts scanning and encrypting files on the local device. And, in the case of a malicious link, the attacker can leave a Trojan horse on the web page, so that when the recipient clicks the link to the web page, the ransomware will be quietly downloaded.
Typical variants: Locky, Cerber, GlobeImposter, and CryptoLocker
3. System vulnerabilities
Attackers launch attacks through known system or third-party software vulnerabilities, by searching for and exploiting vulnerabilities in a device’s OS or applications with exploit kits. This was the case in 2017 during the WannaCry cyber-attack. At the time, Windows had a vulnerability known as EternalBlue, which WannaCry exploited to infect 900,00 hosts across a number of enterprise intranets in a single day.
Typical variants: WannaCry and Satan
4. High-risk ports
The service mechanism of certain ports is a point of entry for hackers to launch attacks. WannaCry is a self-replicating ransomware that exploited the Windows vulnerability of port 445, which is one of several common high-risk ports, including 135, 139, 445, 3389, and 5800/5900.
Typical variant: WannaCry
5. Supply chains
Attacks inject malicious code during software development and upgrade. Malicious virus then infects the customer’s apps or updates, bypassing the scanning software of traditional security products. Previously, Petya ransomware, which hit at least 65 countries, spread by hijacking the Medoc software update.
Typical variant: Petya
6. Watering holes
Malicious code is implanted into popular or authoritative websites, and victims can be caught when they visit the website or download related files.
Typical variants: Cerber and GandCrab
Often, a ransomware attack spreads through a combination of these attack methods.
Ransomware Attack Process
The characteristics of common ransomware viruses show an attack process that is divided into four stages: sniffing, invasion, spread, and ransom.
Step 1: Sniffing
Hackers aim to collect information from an organisation and/or IT system, using network sniffing tools to locate vulnerabilities in the target IP address, OS information, and open ports. Through public means or internal members, hackers collect information about their targets, including departments, leaders, email addresses, phone numbers, and more. Ransomware can lay dormant for weeks to months or even years before inflicting any damage, and is the result of careful planning and long-term targeted detection of the target.
Step 2: Invasion
Using various intrusion methods (including weak-password attacks, phishing email attacks, web and database vulnerabilities, zero-day exploit, remote access, and social engineering), hackers exploit system vulnerabilities to enter the system and implant the virus. This process includes social engineering methods to impersonate public or executive mailboxes, sending phishing emails, masking malicious scripts or programs as common files, with the aim of tricking victims into downloading and running the files. Other methods to access internal servers include bribery and coercion, or using USB flash drives and Wi-Fi networks that implants ransomware into the system.
Step 3: Distribution
After infiltrating a host, the attacker does not run the ransomware immediately, but waits to obtain higher permissions, and then employs multiple attack tools — vulnerability exploit, password extraction, and remote control — to access the entire network. This lays the groundwork for spreading the malware throughout the target network to infect more hosts, in a purpose to find the core data that is the most valuable. Ransomware stays hidden in the background and does not launch the attack until the target is locked on, and as a result, administrators are often unaware of infected devices.
Step 4: Ransom
By the time ransomware is ready to unveil itself, it has likely already encrypted or stolen sensitive data, sending a ransom message that threatens the company to pay a ransom. It is worth mentioning that before encrypting data, attackers will also search for all clean backups and encrypt them to prevent victims from restoring data. Once a ransomware strikes, the victim is left with no other choice but to pay the ransom or abandon the data.
Coming Soon: The True Cost of Ransomware
By Advertorial Desk
(Latest Update December 12, 2023)
|



